Purple Team Part 1: Improve your defensive success with Purple Team exercises
What happens when the Blue and Red team joins forces? Learn about how Purple Team testing can improve your organisations' security posture.

Written by:

Want to know more about this topic? Read our Purple team Part 2 blog post.
Effective cyber defence requires protection and the ability to detect and respond to threats. Performing Purple Team exercises is an excellent approach to testing and improving these capabilities through collaboration. Purple Team exercises enable an organisation to measure and verify that it can detect and respond to real attacks and use this information to immediately improve its defensive security capabilities.
TL;DR
If you are interested in detection and response or responsible for this in an organisation, this blog post will tell you why Purple Team exercises should be on your radar. In this blog post, we'll let you know why that is, describe the concept of Purple Team exercises and introduce the mnemonic Purple Team platform.
Over the last year, we've developed Purple Team exercises as a service and delivered numerous exercises that have proven effective in advancing organisations' defences. Purple Team is a relatively new concept and service, but as we are deeply committed to improving the security of our organisations, it's time to share what we have learned. We have identified three main benefits of Purple team exercises:
- Measure your ability to detect attack techniques used by threat actors in real attacks
- Improve your response time to attacks by practising real scenarios
- Track test results over time to see improvements in visibility, detection, and response
What is this "Purple Team" anyway?
Introduction
The main purpose of a Purple Team exercise is to get the attacking (Red) and defensive (Blue) teams working together to improve an organisation's cyber defence. There are some challenges with achieving this today:
- The distance between the teams is too big
- Measuring detection capability is hard; metrics for defensive success are lacking
- Reproducing attacks to trigger detection is challenging and time-consuming
Purple Team exercises try to address these challenges by:
- Facilitating collaboration between the Red and Blue Teams
- Designing quantifiable, repeatable exercises
- Reproducing detection triggers at scale through automation
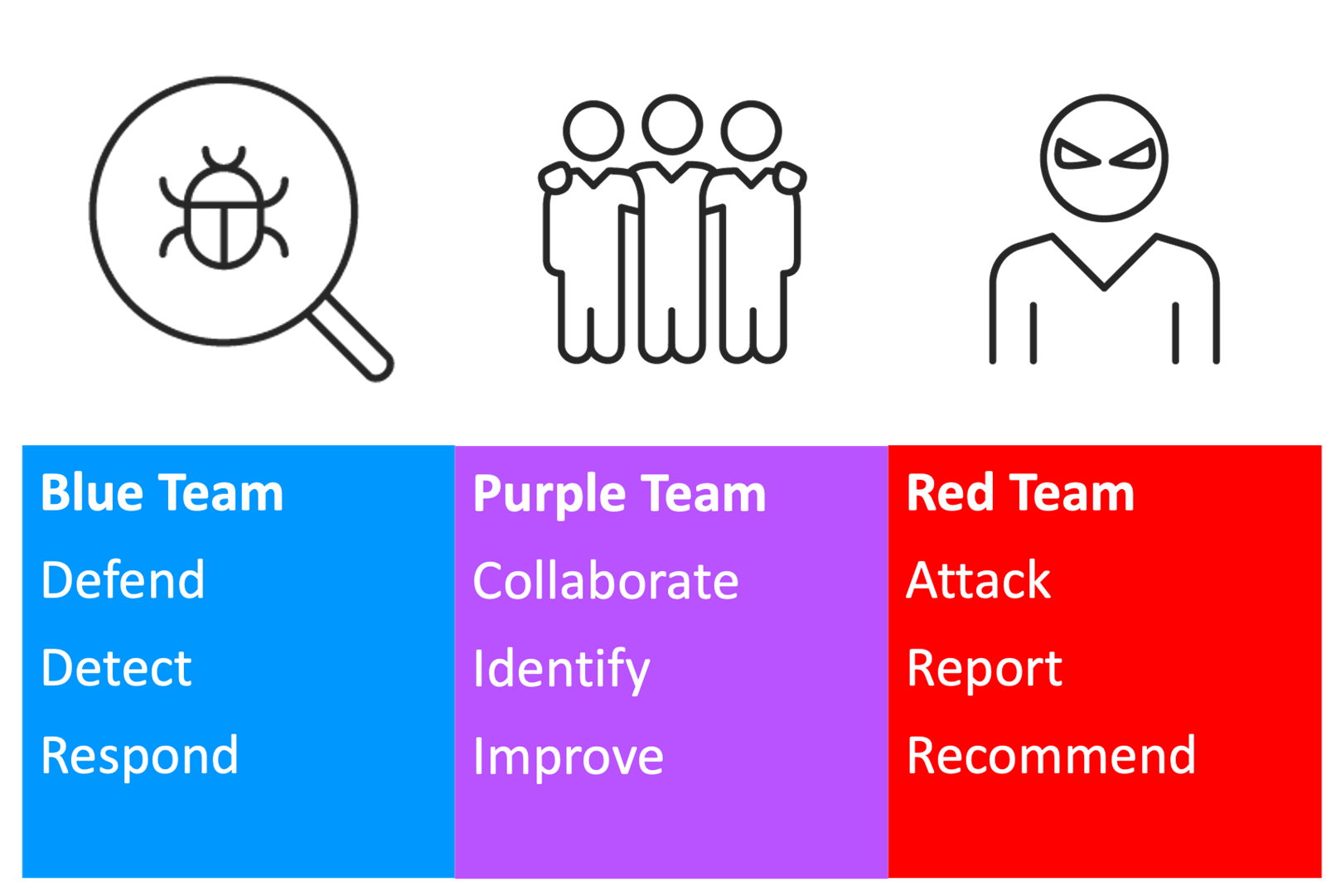
Purple Team exercises aim to assess and improve an organisation's capability to detect and respond to real cyber-attacks. They involve Red Team members simulating attacks and Blue Team members detecting and responding to them, with the two teams collaborating as the temporary Purple Team. The figure below illustrates the roles of the Blue and Red Teams and how they make up the Purple Team through collaboration.
Our definition
Purple Team exercises are a relatively new concept. Our Red Team has not found a standard definition or ideal "Purple Team" reference point. Organisations often mean wildly different things when they say Purple Team, and this is a common problem in the cybersecurity industry. We had to step back and find a clear, concise definition. While "Purple Teaming", applying the word Team as a verb, is sometimes used to separate it as a concept instead of a fixed theme, we wanted to go further.
We found the book Purple Team Strategies by David Routin, Samuel Rossier, and Simon Thoores and the document Purple Team Exercise Framework from Scythe. Both are excellent primers to Purple Team as concept and by using these to gain a better understanding of goals and methodology, we arrived at the following single-sentence definition:
Purple Team exercises are security assessments to facilitate training and measurement of specific threat scenarios and detections for the target organisation.
Beyond landing a standard definition, we also had to develop a robust method, a common framework for how these exercises are planned, executed, reported and, most importantly, used to improve the organisations we test. We found two methods:
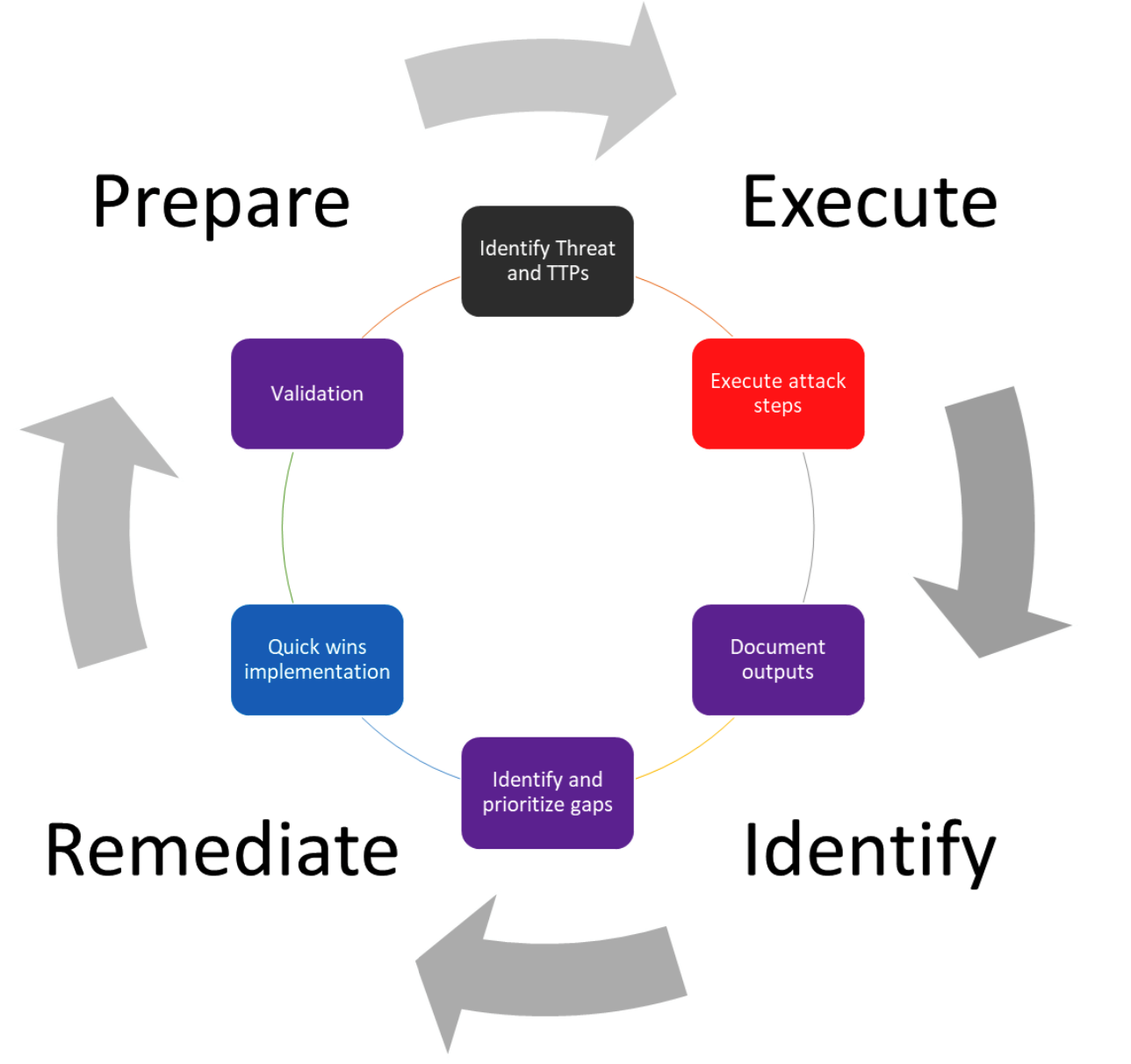
The Prepare, Execute, Identify, and Remediate (PEIR) method is from The Purple Team Strategies. It represents a Purple Team method where both the Red and Blue Teams are involved, and the Blue Team is engaged in the exercise from the preparation stage. The following figures represent the high-level process:
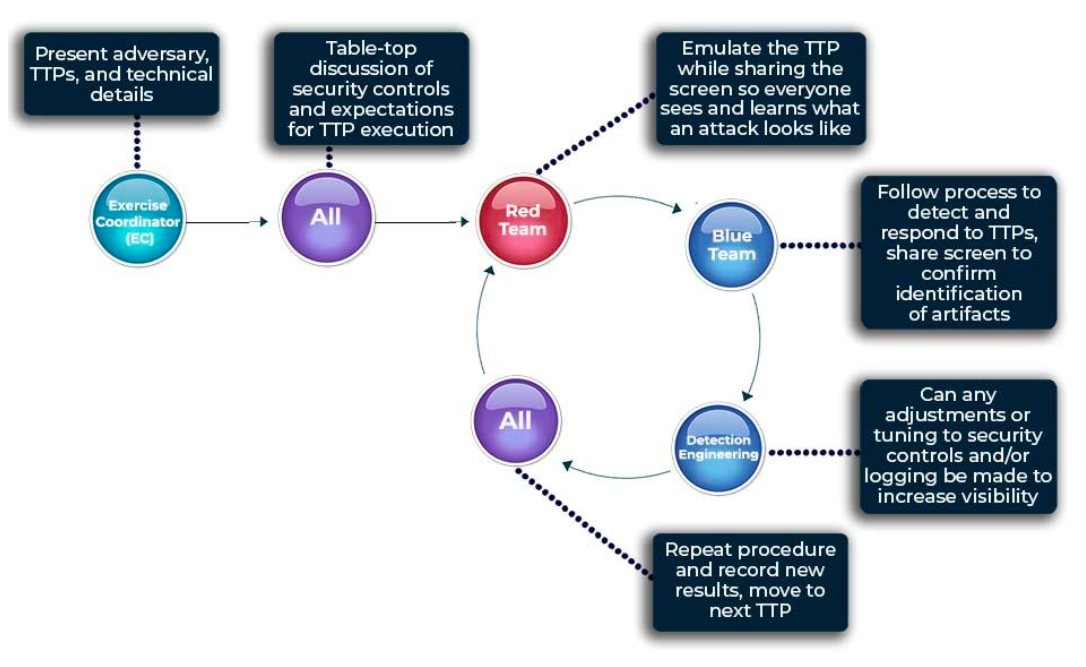
Not too far from it is the method description for Purple Team exercises in the Scythe Purple Team Framework v2. It describes a similar method but provides even more detail on how each Team should operate for each phase of the exercise. We've grown fond of both these methods and apply their concepts to our Purple Team method.
What we have done so far
Throughout 2022 and early 2023, we've performed tens of Purple Team exercises in Norway and internationally. We're also satisfied with the breadth of sectors we've had the chance to perform Purple Team exercises with, including:
- Finance
- Retail
- Health
- Managed service providers (including ourselves)
- Public sector organisations
Through these exercises, we have had the chance to collaborate with some talented Blue Teams and SOCs, who have all been highly committed to integrating themselves into the testing and improving their organisations' detection capabilities. Their response to Purple Team exercises has been overwhelmingly positive. In some organisations, the improvements were so significant that they immediately invited us to perform more exercises. Let us look at our most essential and visible change: the mnemonic Purple Team platform.
The mnemonic Purple Team Platform
Vectr, made by SRA, is a "true" Purple Team platform, meaning its sole purpose is planning, executing and reporting Purple Team exercises. The idea with Vectr is that both the Red and Blue Team and the organisation have access and can see everything at all times. Vectr supports all our test scenarios, and we can design custom scenarios for our customers. It quickly solved many of our challenges with how we did Purple Team exercises in 2022 and gave us a much better way of performing them at scale.
We want to mention that VECTR is an officially licensed product and we have an enterprise license agreement with SRA for its usage. So while Vectr is distributed for free by SRA for internal use, we encourage being good enterprise partners if you are using Vectr in a consultancy solution like we are. We hope this agreement allows SRA to get more funding for VECTR, grow the development team, and make more features faster. Further down in this blog post, we describe our collaboration with SRA in further detail.
How we are using Vectr
The mnemonic Purple Team platform with Vectr as the backbone is how we now coordinate nearly everything related to Purple Team exercises. We provide both the Red Team and Blue Teams with access to the platform so they can collaborate in real-time, all the way through the planning, execution and reporting stages of a Purple Team exercise. We have prepared a range of attack simulations we can run to practice detecting and responding to common attack scenarios and attacks on specific platforms such as Active Directory, or we can run custom tests to trigger specific detection controls. In summary, the mnemonic Purple Team platform:
- Tracks Red and Blue Team testing activities in fine detail
- Enables full transparency and collaboration between teams in real-time
- Provides recommendations and improvements for detection and response
- Provides clear and demonstrable measurements for management
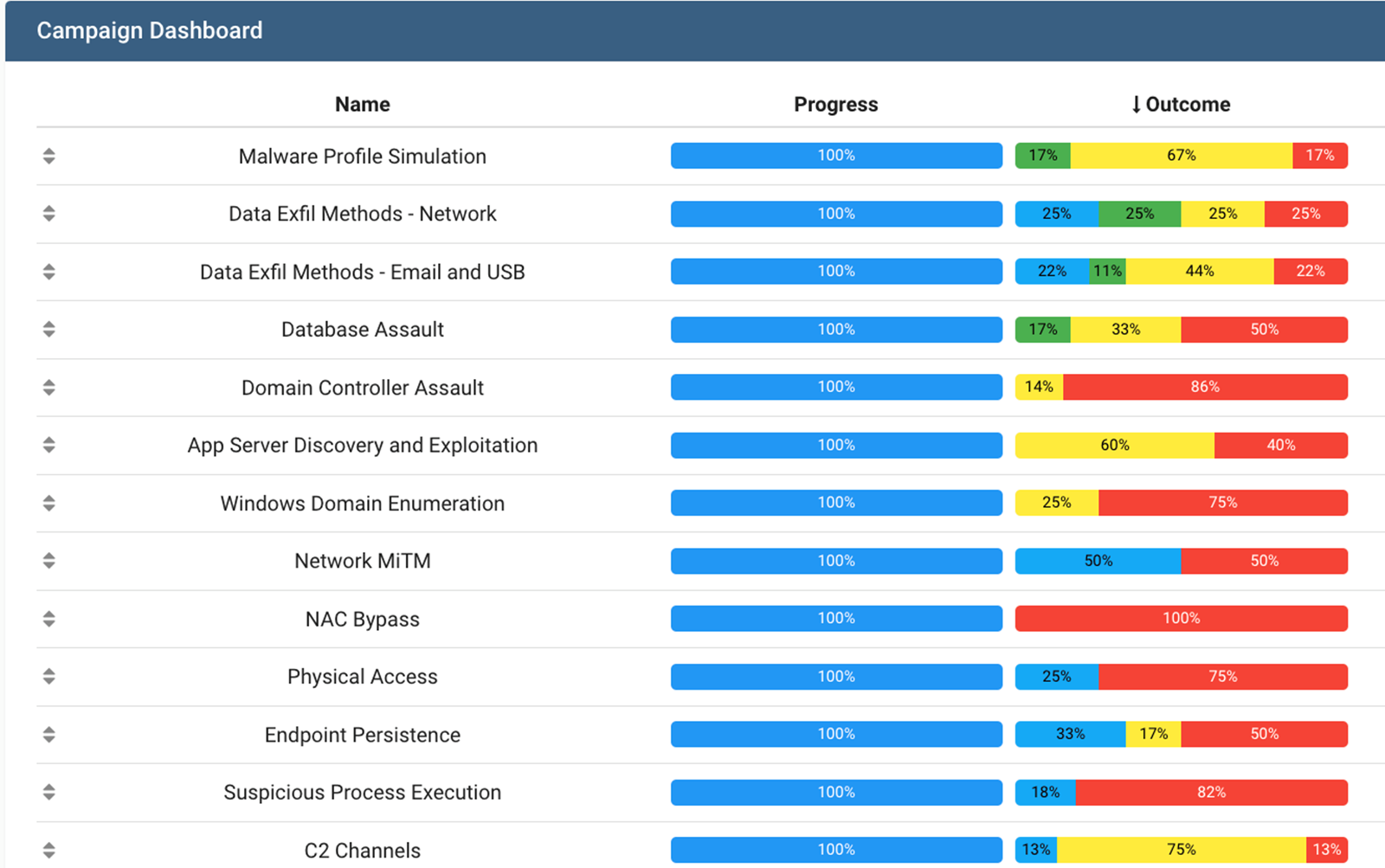
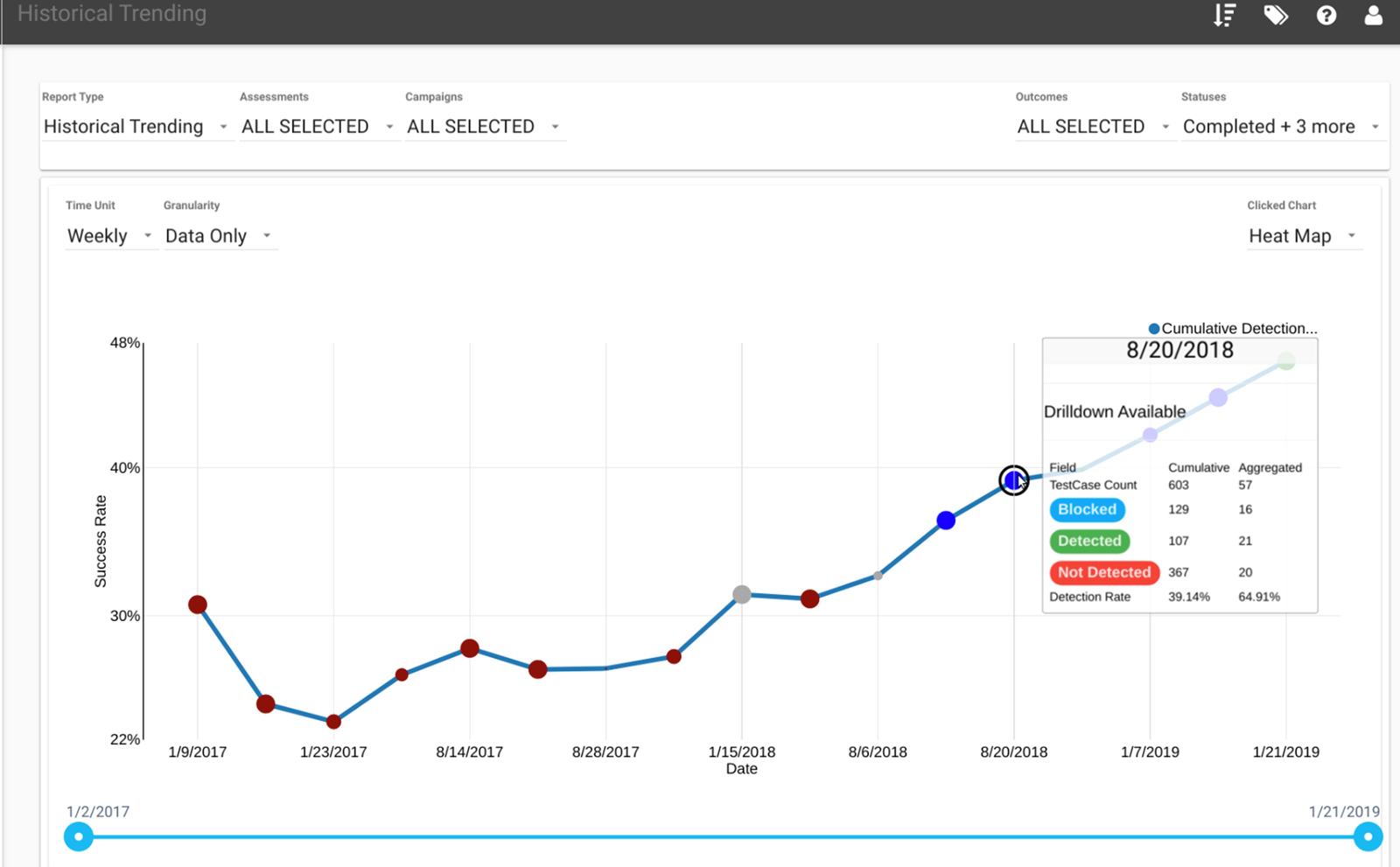
A campaign dashboard displays ongoing Purple Team exercises, their progress and outcomes.
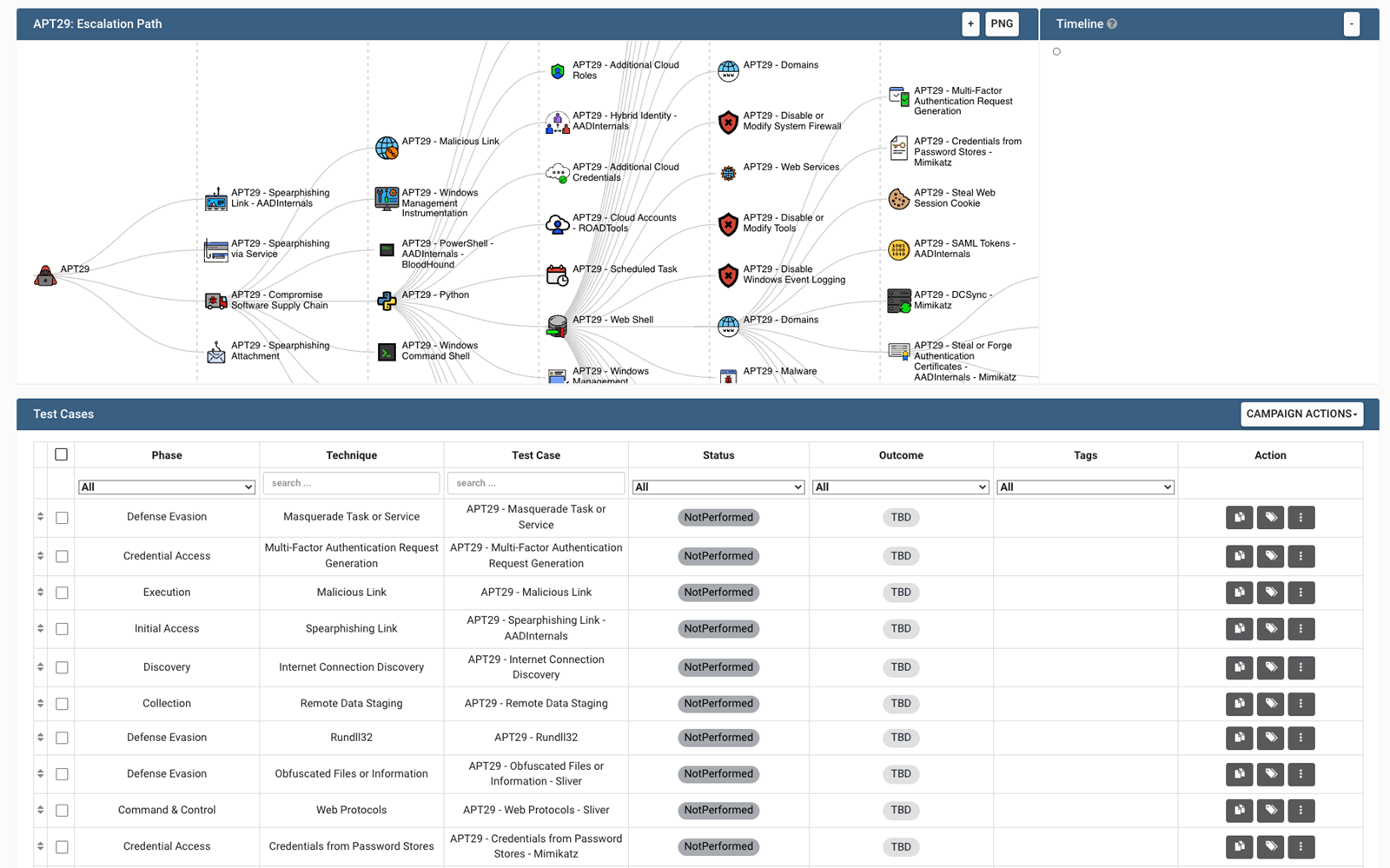
Each campaign has a range of test cases, and we manage each case in fine detail. The Red and Blue Teams have access to everything, and all parties see the execution and reporting in real time. Test cases can be changed or adapted to address new test scenarios or constraints immediately, even during testing. The test case overview also provides a visual "Escalation path" diagram showing each test case in the Mitre Enterprise Tactics kill chain.
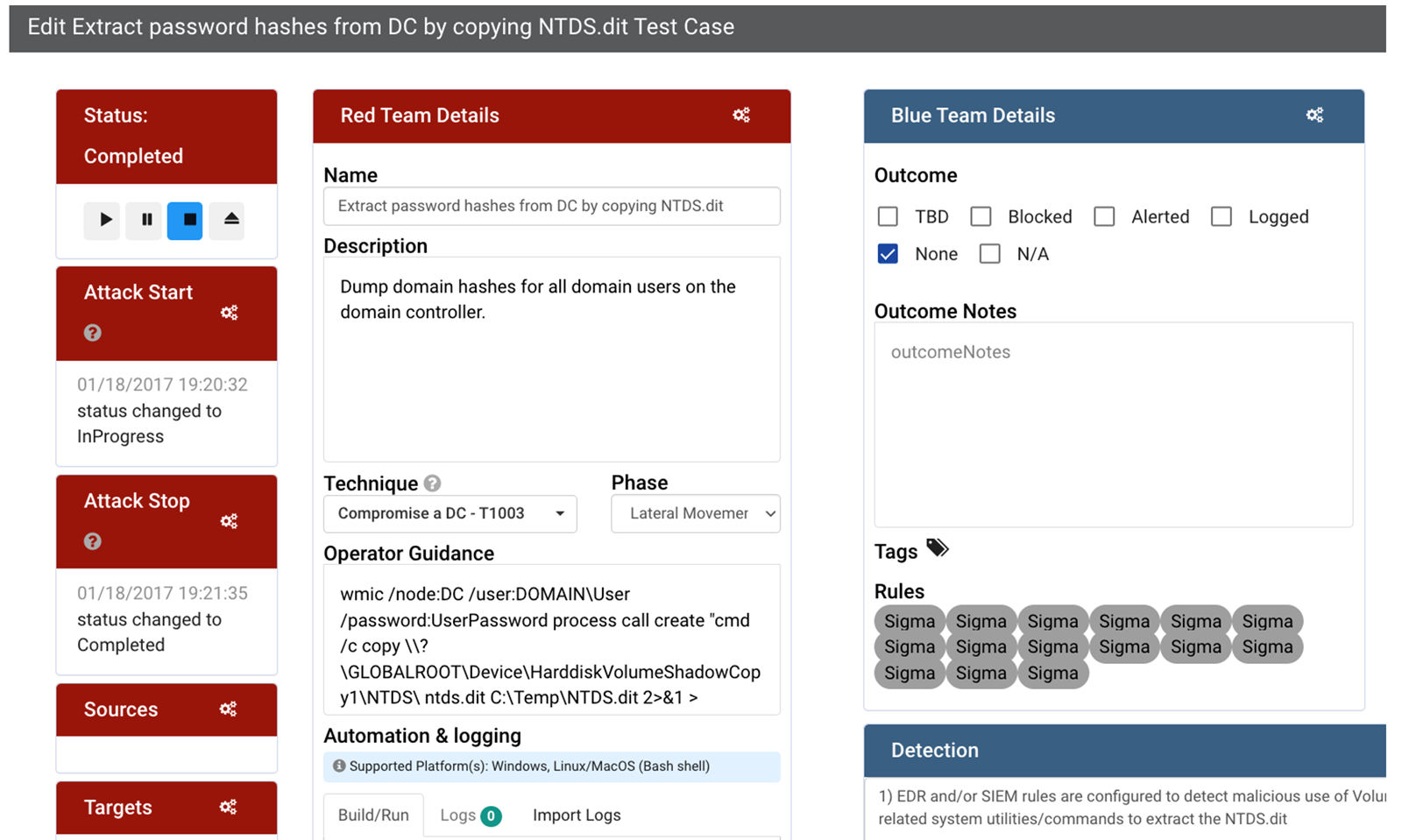
Each test case in a campaign has a Red and Blue side, where the Red Team adds their test case execution details, and the Blue Team adds their results from detection and response, indicating whether they have Blocked, Alerted, Logged, or maybe not even seen the event at all.
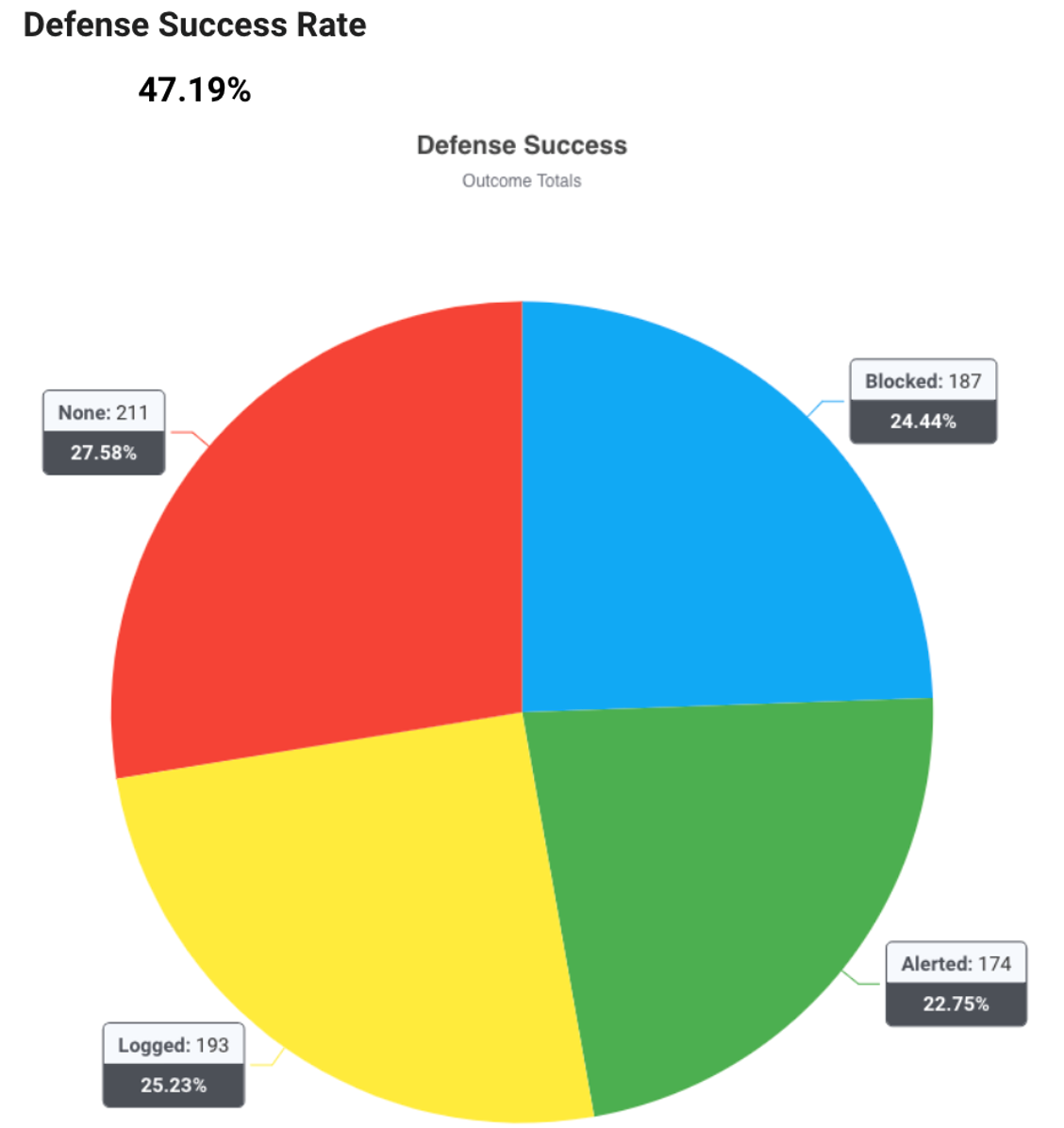
All reporting is available on the Purple Team platform itself. Our tests have shown that quantified defensive scoring leads to the most improvement. With the built-in reporting features in Vectr, it's easier than ever to get a clear overview of defensive success with clear metrics such as blocked, logged, alerted and not detected.
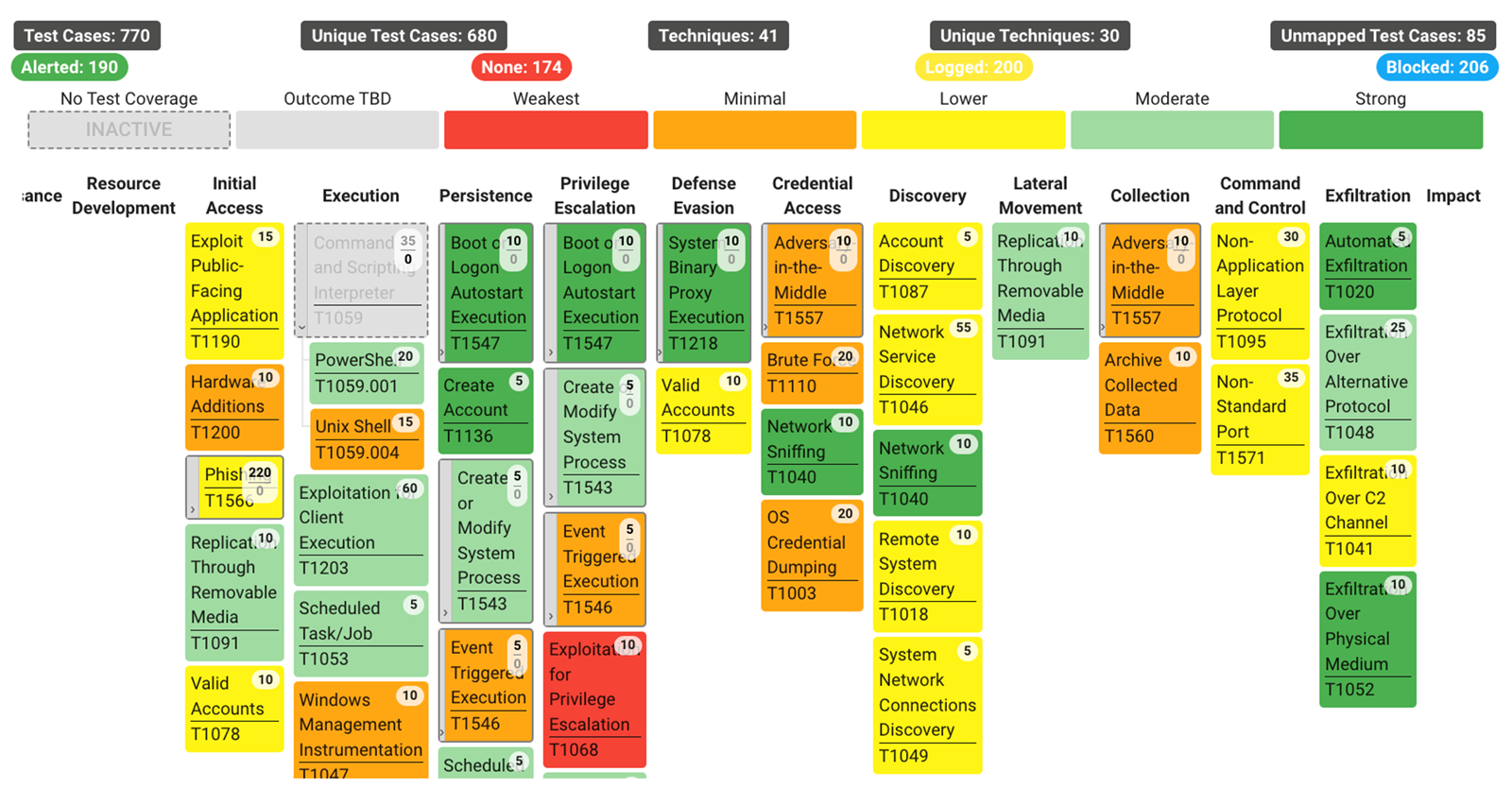
A range of presentation options is available, from sector diagrams of coverage, test case drill-downs, indicators of compromise and, as shown below, a heat map showing the organisation's coverage of Mitre ATT&CK TTPs dynamically.
Additionally, the platform can display historical data for repeated exercises, highlighting improvements to detection and response over time.
What's most important here is that the results of the exercises are measurable. Reporting is clear and concise in various formats suitable for everything from executives to those developing detection signatures. We are confident this platform is the right way to deliver Purple Team services at scale.
mnemonic Purple Team program
The first thing we do is host a meeting with the stakeholders and Blue Team members, and our or our customers' Threat Intelligence group to scope the exercise. Together, all are involved in scoping the test to target:
- The right platforms, systems or areas of the organisation, according to stakeholders
- Known detection controls, but also unknown or known missing capabilities
- The correct areas or security controls according to threat intelligence
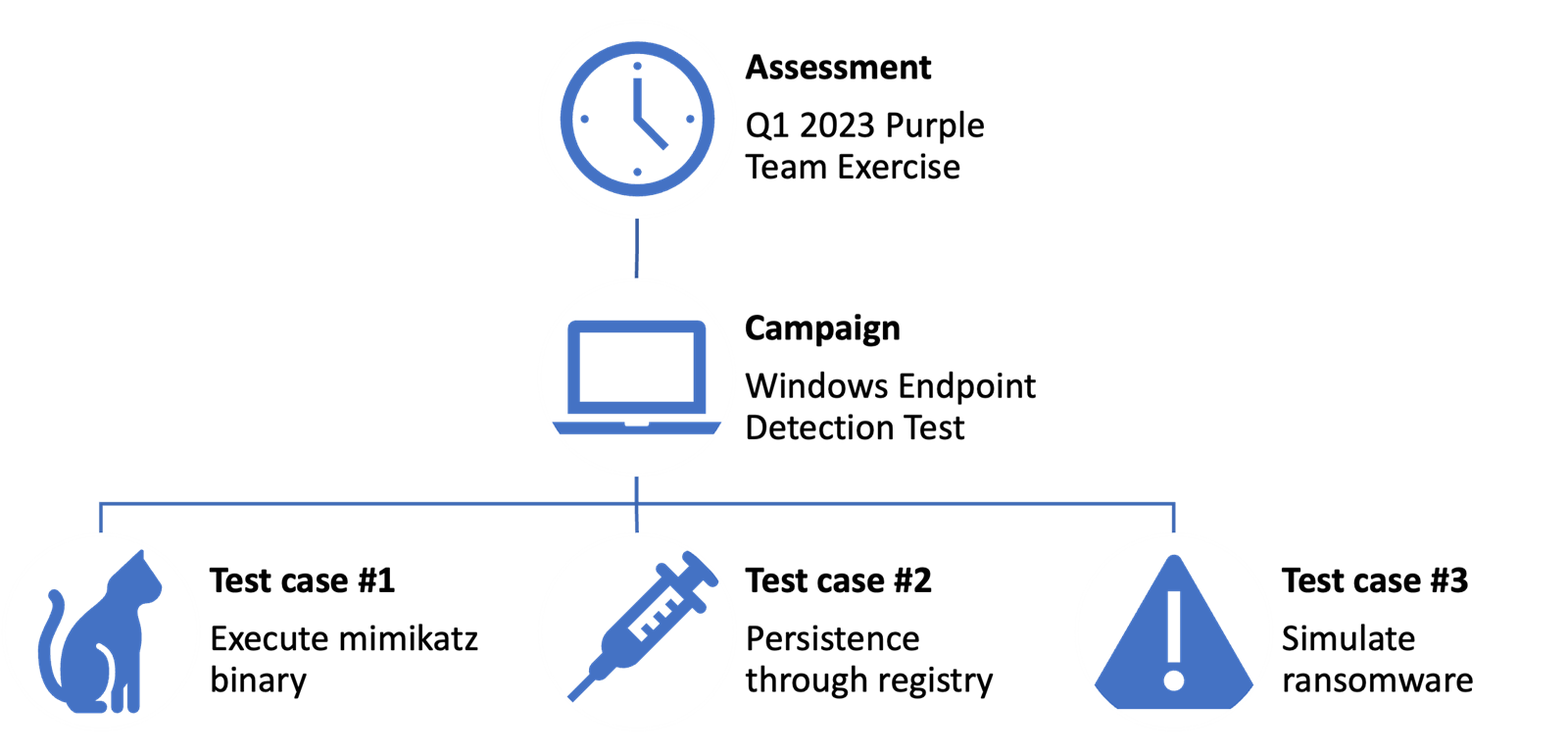
A Purple Team exercise follows a design hierarchy like this, with an example figure below.
- Assessments – a group of exercises, or a planned sequence of tests
- Campaigns – A single exercise or group of attack techniques to test
- Test cases – One simulated attack technique
- Procedure/operation – Typically a PowerShell one-liner, or similar implementing the specified attack technique, which we can automate.
- Test cases – One simulated attack technique
- Campaigns – A single exercise or group of attack techniques to test
Our Red Team uses the Purple Team platform to create a test plan draft, which is then further expanded upon with our Threat Intelligence department in a dedicated workshop. From here on, nearly everything happens on the platform. We establish the test as an assessment, with potentially multiple campaigns, where each campaign typically contains 15-30 test cases.
We then get all the stakeholders and the Blue Team members enrolled into the platform, present the campaign(s) and agree on all practicalities. Typically, we make changes to the test plan until the end.
We start the Execution phase with an execution kick-off meeting to land all the final details. Once the Red Team executes, the Purple Team platform is open on everybody's screen. The test case execution details start pouring in rapidly as the Red Team is testing, both automatically and manually. Each day of testing starts and ends with a short debriefing meeting so that everybody involved is aligned on the test progress.
After testing is complete, a comprehensive Blue Team debrief is performed. Based on this, the Red Team develops a report based on the findings in the platform. The Red Team presents the report to stakeholders, with comments from the Blue Team and recommendations from the Red Team.
The Blue Team follows up with implementing changes, which can involve improving existing detection and developing new detection capabilities. They sometimes even initiate more extensive strategic improvements with the help of stakeholders, such as updates to the defensive technologies, improvements to procedures or re-testing of specific controls. Once the Blue Team is satisfied with their improvements, we host a follow-up meeting between the Red Team, Blue Team and stakeholders. This meeting ensures the organisation identify potential improvements and plans future work, re-testing or additional testing.
Collaboration with Security Risk Advisors (SRA)
We love Vectr and want to acknowledge the great work done by its developers Security Risk Advisors (SRA). We recently got involved in the Vectr community on Discord, and by contributing there and on GitHub with testing and reporting issues, we got in contact with SRA. We quickly realised we had much in common and could improve each other.
SRA distributes Vectr as free software for educational and internal Purple Team use, which is fantastic. As our Purple Team offering is largely based on Vectr, we have an enterprise license agreement with SRA for consultancy usage. As mentioned earlier in this post, this allows SRA to grow the Vectr development team, develop new features and also gives us priority support and assistance. mnemonic offers a range of services, including threat intelligence. Our TI department was very eager when we put their carefully designed Threat Events™ (typical attack scenarios) into Vectr and realised we could automate and run Purple Team exercises from these scenarios. Together with SRA, we are finding ways to make Purple Team exercises even more available and show organisations how they can achieve defensive success with Vectr.
What we love about Vectr is how it has enabled us to start delivering Purple Team exercises at scale, and our customers and the Blue Teams we work with immediately embrace it just as quickly as we have. Everything works better than before; planning, executing, reporting and follow-up are far more easily tracked, and it's much easier to see the actual improvements the organisations are making.
Want to know more about this topic? Read our Purple team Part 2 blog post.
If you want to learn more about our Purple Team exercise offerings, please check out our Solution Brief for Purple Team exercises and contact us for a live demo.
Author