EU Cybersecurity Regulations 2025
Overcoming challenges and embracing compliance

Written by:


As 2024 has ended, it’s time to prepare for the challenges of 2025. At mnemonic, our objective remains clear: removing the guesswork from cybersecurity. To support this, we’re sharing insights on upcoming EU legislation shaping the digital landscape and lessons learned from our work on EU initiatives aimed at a more secure future.
Some of the legislations cover critical and essential services which inhabitants of the union rely on. The common denominator for these service providers is that they have been around for a long time, and have adapted to meet the needs of their users. More often than not, this means there are core parts of the organisation supported by outdated and unsecure-by-design technologies which are hardened by new gatekeeping layers. Technology has evolved from a support function to become the backbone of essential services. There has also been a “notable escalation in cybersecurity attacks, setting new benchmarks in both the variety and number of incidents, as well as their consequences” (ENISA Threat Landscape 2024). Simultaneously, digital adoption accelerates, expanding the overall attack surface. Our shared digital future is thus influenced both by legacy issues and emerging threats.
To address these challenges, the EU is implementing legislation to ensure a common baseline for security and resilience. These measures emphasise foundational practices like value chain risk management, resilience, incident response, and information sharing.
A shared digital future
To operate within the EU, it is likely your business must comply with one or more of these regulations, and we’re here to help you navigate their complexities.
While the legislations can seem fragmented, the response to them should be done holistically, from each of the individual organisations operating within the union. When everyone does their part society as a whole gains valuable resilience. Even though many of the laws have a gradual roll-out, and some have not yet been implemented, an effort to adhere to them should be in focus as we take our first steps into 2025. Organisations should expect an increased need for self-assessments, internal, and external audits. The path to compliance can be structured through planning and by documenting the processes that are needed for each of the legislations. So, what are a few of the most important legislations that are in scope for this?
- NIS2 – Network and Information Security Directive v.2
-
DORA – Digital Operational Resilience Act
-
CER – Critical Entities Resilience Directive
-
AI Act – Artificial Intelligence Act
-
CRA – Cyber Resilience Act
-
CSA – Cybersecurity Act
-
CSoA – Cyber Solidarity Act
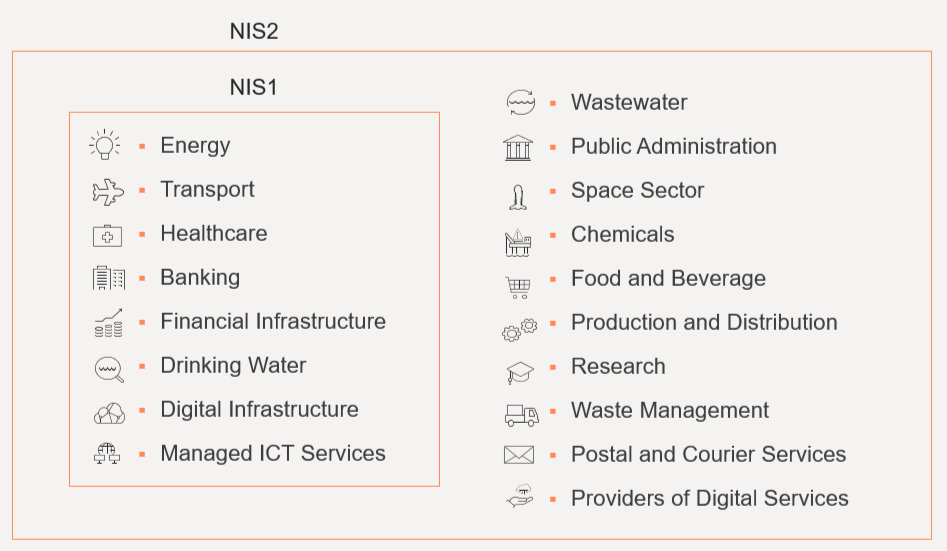
1. NIS2 – Network and Information Security Directive v.2
Objective: Enhances cybersecurity and resilience across the EU by setting stricter requirements for a broader range of sectors
Scope: Expands from NIS to include more sectors, such as Public Administration, Waste Management, and others
Requirements: Mandates improved risk management, incident reporting, and security measures to ensure the resilience of essential and important services.
2. DORA – Digital Operational Resilience Act
Objective: Strengthens the digital operational resilience of financial entities within the EU.
Scope: Applies to a wide range of financial institutions, including banks, insurance companies, investment firms, and their critical third-party ICT service providers.
Requirements: Requires entities to implement robust ICT risk management frameworks, conduct regular testing, and ensure effective incident reporting and response mechanisms.
3. CER – Critical Entities Resilience Directive
Objective: Enhances the resilience of critical entities providing essential services against various threats, including natural disasters and terrorist attacks.
Scope: Targets critical infrastructure sectors such as energy, transport, health, drinking water, and digital infrastructure.
Requirements: Obligates entities to conduct risk assessments, implement resilience measures, and report disruptive incidents to competent authorities.
4. AI Act – Artificial Intelligence Act
Objective: Regulates AI systems within the EU to ensure they are safe, transparent, and respect fundamental rights.
Scope: Applies to providers and users of AI systems, with stricter obligations for high-risk AI applications in areas like healthcare, law enforcement, and employment.
Requirements: Mandates risk assessments, data governance measures, transparency obligations, and human oversight for high-risk AI systems.
5. CRA – Cyber Resilience Act
Objective: Establishes cybersecurity requirements for products with digital elements to ensure their security throughout their lifecycle.
Scope: Covers manufacturers and distributors of hardware and software products placed on the EU market, including those developed outside the EU but sold within the union.
Requirements: Requires hardware and software products to be designed securely, regularly updated, and for vulnerabilities to be addressed promptly.
6. CSA – Cybersecurity Act
Objective: Strengthens EU’s regulatory role and establishes a voluntarily cybersecurity certification framework to enhance trust in ICT products and services across the EU.
Scope: Applies EU-wide, offering a common certification framework for ICT products, services, and processes to ensure secure and trustworthy digital products for consumers and businesses.
Requirements: Introduces voluntary certification schemes with three risk-based levels to certify cybersecurity resilience throughout the product lifecycle. It complements CRA by providing a unified certification process for products, thus facilitating cross-border trade and reducing security compliance barriers.
7. CSoA – Cyber Solidarity Act
Objective: Enhances the EU's collective capability to detect, prepare for, and respond to cybersecurity threats, fostering stronger solidarity and resilience across member states.
Scope: Focuses on entities in critical sectors, establishing a network of national and cross-border hubs for real-time threat detection and incident response.
Requirements: Mandates coordinated preparedness testing, advanced data collection for situational awareness, and the establishment of an EU cybersecurity reserve to support incident response. Implements border-crossing Security Operation Centers (SOCs) to improve threat response capabilities across the EU, ensuring robust and coordinated resilience in the digital ecosystem.
A collective effort
Recurring themes of these legislations focus on resilience and preparation for incident handling. They emphasise risk management, particularly within supply chains, where accountability lies at the management level.
Another key aspect is fostering cooperation through information sharing across the union, while mandating public entities to gather and receive information about incidents and system downtime. We believe this will accumulate into centralised vantage points, providing deeper real time insights into the EU’s digital landscape. These measures are crucial steps forward, reflecting the EU's response to rising cybercrime and cross-border cyber-incidents.
It is vital for all organisations to understand their responsibilities, starting by identifying vulnerabilities, and working towards becoming more resilient through well-timed actions. As many of the legislations adopt a risk-based approach, the measures can be proportionally applied based on the organisation’s judgment.
Taking steps to meet the requirements could also mitigate potential non-adversarial cyber consequences, as the measures address a broad range of scenarios. To achieve holistic compliance, organisations should begin mapping out the regulatory requirements that apply to their sector. This effort should be led by management, who are positioned to appoint roles and oversee the integration of each regulation into their existing systems and governance models.
A demanding task
Organisations may face challenges or obstacles in complying with the new EU legislations. A few we've encountered include:
- EU's Goal vs. Reality: While the EU aims to harmonise cybersecurity efforts across member states, practical implementation varies because of differences in how local governments interpret and enforce the rules. This creates inconsistencies in compliance requirements.
- Types of Legislations: Acts generally leave little room for interpretation, making them more uniform, whereas Directives allow member states to adapt them more flexibly, leading to "local creativity" and variation.
- Challenges for Cross-Border Organisations: Businesses operating in multiple EU countries must navigate these differing requirements, which complicates compliance. They also have to account for proportionality principles that vary by context, further muddling clarity.
- Integration and Complexity: Each new legislation adds unique requirements, which may not align easily with existing systems and frameworks, increasing the burden on organisations.
- Source of Complexity: The difficulty doesn’t lie in the technical aspects of implementing the rules but in determining which rules to follow, given the variation and flexibility in interpretation. This "wiggle room" for implementation adds to the perceived complexity.
The harmonisation goal is undermined by local variations in implementation, making compliance for businesses a challenging task of navigating overlapping, flexible, and sometimes contradictory requirements.
Planning for what’s ahead
Management will increasingly become responsible for the overall security of their organisation, requiring them to actively engage in and drive risk management efforts. Ideally, this accountability will encourage greater resource allocation to secure and strengthen critical processes and functions.
Raising awareness:
Efforts should also focus on raising general awareness of technology and security among employees. This will empower employees to contribute more efficiently to the management of the risks an organisation faces. Significant value can be found by actively seeking and consolidating the knowledge quietly held by employees. Blind trust in written policy might overlook discrepancies that can occur during implementation and execution, so having insight into how the company operates in practice is a key ingredient for effective risk management.
Asset inventory:
To understand the foundation of the business, management should assess how critical pillars would be affected if compromised. This should be paired with a comprehensive inventory of all assets, software, and hardware in use. However, many businesses still have a fragmented understanding of their digital infrastructure. If they don’t know what their assets are or how they’re used, managing risks becomes impossible.
Identifying processes:
Additionally, management needs to identify and understand what key processes and functions support their overall goals. Many of these functions are often either supported by third party solutions or entirely outsourced. To ensure there is no dilution of responsibility, an effort has to be made to ensure different vendors understand what kind of requirements need to be fulfilled. These vendors do not only supply products and services; they also introduce new risks to be understood and addressed. Though visibility into these risks is limited, management should strive to identify them in order to understand both positive and negative risks.
Creating an incident response plan:
If negative risks are to materialise, a structured incident response plan has to be ready. With the new legislations, some organisations now have to be rigged to report on incidents shortly after detection, and then follow up with a more detailed report of these incidents. Our experience is that this is not a task that is easy to prioritise when the organisation is busy reverting to a normal state. This function needs to be planned and exercised in advance in order to facilitate compliant cooperation and communication.
Continued revision:
While these insights can contribute to a solid foundation for future compliance to the upcoming legislations, it’s important to treat compliance as an ongoing process. All of the requirements stress how they are not a one-time checklist, as they should be monitored and evaluated on an ongoing basis. The same goes for the technical solutions supporting the security mechanisms. Regular input from threat intelligence and technology advancement is needed to ensure a solid security posture throughout the years ahead.
Compliance builds security, security builds customer trust
The upcoming legislations are expected to demand increased resources and attention. Digital security in the EU is not going to be as haphazard as it has been before. The regulations are there to remove unreliable actors that can topple the systems our society depends on, leading to multiple reasons for an organisation to jumpstart its compliance journey. The significance and impact of achieving compliance for your company include:
- Navigating the complexities of the requirements
- Contributing to the overall security in Europe
- A competitive advantage when the EU takes further steps into a security-first era
- Noncompliance can result in time consuming audits and substantial fines
We hope that these insights have been useful, if you have any further questions – please reach out!